Ethical Hacking Programs
The ANSI accredited Ethical Hacking program is primarily targeted at security professionals who want to acquire a well-rounded body of knowledge to have better opportunities in this field. Acquiring a Certified Ethical Hacking Certification means the candidate has a minimum baseline knowledge of security threats, risks and countermeasures. Guide to Ethical Hacking: Tools and Free Tutorial on Ethical Hacking What Is Ethical Hacking? Computer hacking is a practice with many nuances. Intent, whether benign or malicious, is often in the eyes of the beholder. When examining the root cause of a website hack or application exploit, it pays to follow the money. Ethical Hacking With A Security Scanner. Use the Netsparker web application security scanner and its ethical hacking software and tools to perform automated security scans on your web applications and identify security issues before malicious hackers find and exploit them. 30+ Hacking Experts have compiled this list of Best Ethical Hacking Course, Tutorial, Training, Class and Certification available online for 2019. It includes both paid and free resources to help you learn Ethical Hacking and these courses are suitable for beginners, intermediate learners as well as. The ANSI accredited Ethical Hacking program is primarily targeted at security professionals who want to acquire a well-rounded body of knowledge to have better opportunities in this field. Acquiring a Certified Ethical Hacking Certification means the candidate has a minimum baseline knowledge of security threats, risks and countermeasures. We have compiled a list of top hacking software and tools of 2019 with their best features and download links. This list is based on industry reviews, your feedback, and our own experience.
- Ethical Hacking Programs For Pc
- Ethical Hacking Software For Windows 10
- Programs For Ethical Hacking
- Ethical Hacking Programs For Free
Overview of Ethical Hacking Tools
Ethical hacking is the act of discovering vulnerabilities and weaknesses of systems and applications by reproducing the reasons and actions of dangerous hackers. Ethical Hacking Tools are simply computer scripts and programs that help us in discovering and exploiting liabilities in various systems like computer systems, networks, and web applications.
Many of these tools are available for use in the market, few of them being open-sourced, while others being paid solutions.
Web development, programming languages, Software testing & others
Top Ethical Hacking Tools and their Features:
Below are some significant ethical hacking tools that are as follows.
1. Burp Suite
Burp Suite is a valuable instrument for web applications as it is helpful in performing security testing for these applications. The many tools provided in this suite work effortlessly together to assist the entire testing process, from an initial analysis of the application’s surface of attack to discovering and exploiting security vulnerabilities.
Features:
- It helps in scanning custom-built applications and open-source software.
- It can perceive over 3000 vulnerabilities in a web application.
- It allows for automatic scanning with the help of its Login Sequence Recorder.
- It provides for a wide span of reports, both technical and compliance.
- It has the provision of built-in vulnerability management.
- It has an automated crawl and scans feature, including an innovative scanning feature for manual testers.
2. Ettercap
Ettercap is the short form for Ethernet Capture. It is a security tool that sniffs out and captures live connections and content filtering. It is used mainly for Man-in-the-Middle attacks. Ettercap can be run on most of the operating systems such as Windows, Mac, and Linux.
Features:
- It supports the division of many protocols, including active and passive division.
- Ettercap has inbuilt features for host and network analysis.
- It includes a feature to sniff out a switched LAN by means of ARP poisoning.
- It is capable of sniffing out an SSH connection.
- Ettercap can inject characters into a server or into a client, all while upholding a live connection.
- Even when there is a proxy connection, Ettercap allows for sniffing out of HTTP SSL secured data.
- Ettercap has APIs which allow us to create custom plugins.
3. Aircrack
AirCrack is a well-known security suite for home and corporate security environments. It works by seizing network packets and then analyzing them to crack the WiFi. It also includes full support for WEP and WPA networks.
4.5 (1,443 ratings)
Features:
- It supports numerous drivers and WiFi cards.
- It supports Windows, MAC and Linux detection for WiFi.
- It has launched a WEP attack known as PTW.
- It has an express cracking speed.
- It has documentation that ranges extensively, from Wiki pages to more.
- It can be integrated with third-party tools.
4. Angry IP Scanner
Angry IP scanner is a lightweight, open-source and cross-platform scanning tool. It scans IP addresses in any range, and also easily scans ports. It uses a multithreaded approach to increase the speed of its scanning. A separate scanning thread is made for each and every scanned IP address. Angry IP Scanner works by pinging an IP address to check if it is alive and then resolving its hostname to determine the scans ports, MAC address, etc.
Features:
- It scans local networks along with the Internet.
- It is an open-source tool, which can be accessed easily.
- The file procured after scanning can be in any file format.
- It can be used extensively with various data fetchers.
- It offers us with a command-line interface.
- There is no need for any installation process.
5. QualysGuard
QualysGuard is a security tool that is used to streamline the security and compliance issues of businesses. It provides critical security intelligence and also automates the various systems for auditing and compliance. QualysGuard can also inspect online cloud systems for performance vulnerability.
Features:
- QualysGuard is a scalable solution in nearly all IT security aspects.
- It does not require us to buy any hardware.
- Critical security intelligence is stored securely in an n-tiered architecture.
- QualysGuard offers us continuous visibility with the help of its sensor.
- The data analyzed is done in real-time.
- It can respond to real-time threats.
6. WebInspect
WebInspect is an automated security assessment tool, that helps us in identifying known and unknown liabilities in the web application layer. It also helps us in checking whether a Web server is configured properly or not.
Features:
- WebInspect tests the dynamic behavior of running applications which in turn helps us in identifying security vulnerabilities.
- It provides pertinent information on a quick look, which helps us to be in control of our scan.
- It uses advanced technologies like simultaneous crawl professional testing.
- WebInspect makes it easy to inform the management of compliance management, trending vulnerabilities, and risk overview.
7. LC4
Formerly known as L0phtCrack, LC4 is a powerful password audit and recovery tool. It tests password strength and recovers lost Microsoft Windows passwords, with the help of methods like a dictionary, brute-force, and hybrid attacks. It also helps in identifying and assessing password vulnerability over local networks and machines.
Features:
- LC4 has optimized hardware including multicore & multi-GPU support.
- Customization is easy in LC4.
- LC4 has a simple method for loading passwords.
- LC4 is capable of scheduling tasks for enterprise-wide password.
- It can correct weak password problems by forcing a password reset or locking the account.
8. IronWASP
IronWASP is a free and open-source tool, which supports many platforms. It is suitable for auditing public servers and applications. IronWASP has a customizable design to help users create their own security scanners. It is GUI-based, with full scans being performed within a few clicks.
Features:
- IronWASP is very easy to use for a beginner as it is GUI based.
- It has a powerful and efficient scanning engine.
- IronWASP reports can be in either HTML or RTF format.
- It can record the Login sequence.
- It examines the application for more than 25 kinds of vulnerabilities.
- IronWASP can detect false positives and negatives.
9. SQLMap
SQLMap automates the process of identifying and testing different kinds of SQL-based liabilities and reporting them. Few of the SQL injection techniques are:
- Boolean-based blind
- Time-based blind
- UNION query
- Error-based
- Out-of-band
- Stacked queries
Features:
- SQLMap supports multiple database servers like Oracle, MySQL, PostgreSQL, MSSQL, MS Access, IBM DB2, SQLite and Informix.
- It comprises of capabilities like automatic code injection.
- It uses techniques like password hash recognition and dictionary-based password cracking.
- SQLMap allows us to view various databases and their user privileges.
- It executes remote SQL SELECT statements and also gives up information about dump table.
Ethical Hacking Programs For Pc
10. Cain & Abel
Cain & Abel is a recovery tool for passwords for Microsoft OS machines.
Features:
- It helps in recovering MS Access passwords.
- It employs methods like sniffing the networks for password recovery.
- It helps in uncovering the password field.
- It cracks encrypted passwords using methods like the dictionary and brute-force attacks.
Conclusion
Ethical hacking tools are evolving over time by making ethical penetration testing faster, more reliable and easier than ever. These tools play an important role in identifying the security defects in applications, enabling the developer to quickly revert the vulnerability and bring the application back to a secure state.
Recommended Articles
This has been a guide to Ethical Hacking Tools. Here we discuss the definition and top 10 tools of ethical hacking with their features. You can also go through our other suggested articles to learn more –
Ethical Hacking Software
In terms of ethical hacking software means gaining unauthorized access to data in a system or computer. The person who carries out online hacking is referred to as Hacker. There are three different types of ethical hacking software which are mentioned below :
- White hat hacker
- Grey hat hacker
- Black hat hacker
White hat hacker is people those who break security for non-malicious reasons. It may be to test their own security system. These people find possible loopholes in ethical hacking software or systems are report them in order to get it fixed. They are also referred to as “ethical hacker”. For eg., A Certified Ethical Hacker (CEH) hired by the corporate firm to find flaws in the ethical hacking software. And those certified ethical hackers are with CEH Certification or Ethical Hacking Certification which is gained by clearing the CEH exam.
Web development, programming languages, Software testing & others
Black hat hacker is people those who break the security of the system or ethical hacking software for malicious reasons or for personal benefits. These people generally form illegal hacking groups and work to break into any secure networks in order to destroy, modify or even steal confidential data such as credit card details, banking details, etc. They are also referred to as “crackers”.
Grey hat hacker people come between white hat and black hat hacker. These people survey the system and find loopholes or any security defects and report it to the administrator. At times the grey hat hacker reports these security flaws to the world instead of a group of people. At certain times they may offer to correct the defect for a fee. These people perform hacking without any personal gain.
So there are various ethical hacking program training or CEH training conducted to teach these types of ethical hacking.
Let’s check more about ethical hacking software
What is Ethical Hacking Software?
A. Cyber Ethics

Cyberethics is a code of behavior for using the Internet. We have seen what does hacker and its type are above. Now, we will look into other terminologies related to cyber ethics.
4.5 (1,443 ratings)
- Phreaker: It is a term coined to describe the activity of a subculture of people who study, experiment with or explore telephone connection networks. Phreaking is closely related to ethical hacking basics of the computer since telephone networks have been computerized. Sometimes it is also called as H/P culture where H stands for Hacking and P stands for Phreaking.
- Script Kiddies: These are people who use scripts or ethical hacking basics developed by others to attack computer systems and networks. It is also referred to as script bunny, skiddie or script running juvenile (SRJ).
- Hacktivists: The term Hacktivists is the combination of two words Hacker and Activists. These people carry out ethical hacking activities such as defacing websites for political reason. Their activities include political ideas and issues.
B. Information Gathering
Information gathering is the initial process as far as ethical hacking basics and investigation are concerned. This involves process such as profiling any organization, system, server or an individual using certain defined process. This is generally used by the attacker and/or investigation agency to get additional information about the victim.
There are different ways through which ethical hacking information can be gathered. Some of them are listed below:
1. Use of Search Engine
It is the general understanding that the search engine will provide certain information about the victim. The ethical hacking basics principle about using the Internet is that ‘one leaves footprints/information everywhere while surfing the Internet.’
This principle is used by the attacker as well as hackers. The attacker will gather information about the system, any loopholes in the existing system and possible ways to exploit it. Investigator will gather information such as the approach used by the attacker to get access to the system. The most powerful search engine is google, yahoo search, MSN live search, AOL search, Ask search.
2. Use of relational search engine
The relational search engine is different than the normal search engine. It gets results from different search engine and makes the relation between those results.
i. Whois Lookup: WHOIS which is pronounced as “who is” is a query protocol that is widely used for querying the official database in order to determine details such as the owner of a domain name, IP address, etc.
ii. Maltego: It is an open source intelligence and forensics application that allows the mining and gathering of information as well as representation of this information in a meaningful way. The graphing libraries allow you to identify key relationships between information.
iii. Reverse IP Mapping: This method is used to find a number of websites hosted on the same server where your software/function is hosted
iv. TraceRoute: It gives useful information such as a number of servers between your computers and remote computers. This is useful for investigation as well as different types of attacks. You can see the route between your system and attacker system using NeoTrace which gives MAP view or NodeView of all nodes between attacker and victim.
Ethical Hacking Software For Windows 10
v. Email Spider: These are automated ethical hacking program which captures email ids using spiders and stores them in the database. Spammers (people who send junk email to a large number of people) are using email spiders to collect a thousand emails for spamming purposes.
C. Scanning
Scanning is the process of finding out any open or close ports, any loopholes in the remote system, servers and networks. It helps in getting details of the victim such as IP addresses,
Operating System used as well as services running on the remote computer.
There are three different types of scanning. These are Port scanning, Network scanning, and Vulnerability Scanning.
Port scanning is most commonly used the ethical hacking program by an attacker to find any loopholes in the system. All systems connected to a LAN (Local Area Network) or to an Internet using modem run many ethical hacking services that listen at well-known and not well-known ports. There are total 1 to 65535 ports available in the computer. The port scanning allows the attacker to find which ports are available.
Open scan (also known as TCP scan) is normally used to program sockets. This is quite an old ethical hacking technique and works more correctly in making a full connection with the server. In order to establish the connection, it makes an authentication using three packets. This mechanism of authentication is called as three-way-handshake.
For open port :
Client –> SYN –>
<– SYN/ACK <– Server
Client –> ACK –>
For close port :
Client –> SYN –>
<– RST <– Server
The advantage of this open scan is that it is easy to program. However, the limitation is that it is very easy to detect and make logs on each connection.
TCP connect() :
- The connect() system call provided by an ethical hacking operating system is used to open a connection to every interesting port on the machine.
- If the port is listening connect() will succeed otherwise the port isn’t reachable.
SYN scan :
- This scanning technique is called half-open scanning because a TCP (Transmission Control Protocol) connection is not completed.
- An SYN packet is sent to the remote computing
- The target host responds with an SYN+ACK packet which indicates the port is listening and an RST indicates a non-listener
NULL scan :
- NULL scan used no flags of TCP header and it sent to the target host
- Closed ports reply to packets with RST
- Open ports ignore packets
NMAP (port scanner):
- NMAP is a powerful utility to scan a large number of ethical hacking tools
- It is available with GUI (Graphical User Interface) and Command Line Interface
- It is supported by a wide range of Operating Systems such as Linux, Mac OS, Windows
- It can carry out SYN scan, FIN scan, Stealth scan, Half open scan, and many other types.
D. Virus, Worms, Trojans and Virus analysis
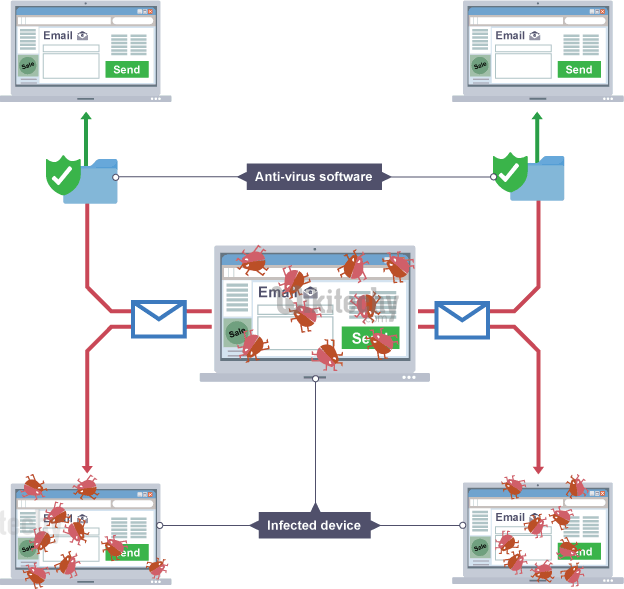
VIRUS (particularly stands for Vital Information Resource Under Siege) is an application or piece of code that replicates itself by injecting its code into other data files or ethical hacking program and has a detrimental effect such as corrupting the system or destroying data.
Export SOLIDWORKS files to pdf and dxf files with the Caddossier add-in from Komdex. Nov 29, 2017 I would like to convert our slddrw files to pdf and keep them in their current location. I have tried using the task manager but it will not let me use wildcards. I want to convert using.pd.slddrw. This will not find just the files containing pd but all slddrw files. When you change the state of a SOLIDWORKS Drawing file using a transition on which the Drawing to PDF Convert task is set, SOLIDWORKS PDM runs the task. The task: Launches a SOLIDWORKS session on the client computer. Opens the SOLIDWORKS Drawing file. Saves the file as PDF. Aug 22, 2019 How to Convert PDF to Solidworks. This wikiHow teaches you how to convert a PDF into a Solidworks document using the Solidworks program on a Windows computer. Solidworks is a 3D program that is most often used by engineers and architects. Apr 04, 2016 From PDF to a model in SolidWorks Ronald Vukoje. Unsubscribe from Ronald Vukoje? Convert a 2D DWG to SolidWorks 3D Model - Duration: 22:18. Cadcast 156,130 views. Convert solidworks file to 3d pdf.
Worms are a standalone malware computer program that replicates itself over ethical hacking basic. As compared to the virus it does not need to attach itself to an existing program.
Trojan (in the context of computing) is any malicious computer program which represents itself as useful in order to persuade a victim to install it on his/her system.
There are several different modes of transmission for these virus, worms or trojans into your system. Some of them are listed below:
- IRC (Internet Relay Chat)
- ICQ (I Seek You – Instant Messaging Program)
- Email attachments
- Physical access (such as connecting infected USD drive or hard disk)
- Infected Browsers
- Online advertisements (such as banners that claim you won the lottery)
- NetBIOS
Properties of Virus
- Your computer or system can get infected even if files are only copied
- It can be polymorphic
- It can be a memory or non-memory resident
- It can be the stealth virus
- Most times viruses carry another virus
- It can even make your system never show outward signs
- It can even stay on your system even though it is formatted
Virus operation phase
Most of the virus operates in two phases i.e. infection phase and attack phase
- Infection phase
- In this phase, the virus determine when and which programs to infect
- Some viruses infect the system as soon as virus file is installed on the system
- Some viruses infect the system at the specific date, time or the particular event
- TSR viruses are loaded into memory and later infects the systems
- Attack phase
- In this phase, the virus will delete files, replicate itself to other systems and corrupt targets only
Symptoms of virus-infected system
- Files/Folder have the strange name than the normal (eg. %$#%% as the file name)
- File extensions can also be changed
- The program takes the longest time to load than the normal
- Systems hard drives constantly runs out of free space
- You will not be able to open some programs
- Programs getting corrupted without any reasons
- System working very slow and sometimes getting rebooted unexpectedly
Types of Virus
– Macro virus: spreads and infects database file
– File virus: infects executable
– Source code virus: affects and damage source code
– Network virus: spreads via network elements and protocols
– Boot virus: infects boot sectors and records
– Shell virus: forms shell around the target host’s genuine program and host it as the subroutine
– Terminate virus: remains permanently in the memory during the work session
Recommended courses
Methods to avoid detection of the virus in Ethical Hacking Software
Keep same “last modified” date
Msi motherboard review. i. In order to avoid detection by anti-virus software as well as users, some viruses use different kinds of deception such as they have the same last modified date as other genuine files or folder.
ii. There are some viruses (especially on the MS-DOS system) that make sure that the “last modified” date of a host file stays the same when the file is infected by the virus.
Avoiding Bait files
i. Bait files (or goat files) are files that are specially created by anti-virus software or by anti-virus professionals themselves, to be infected by the virus.
ii. There are many anti-virus programs that perform an integrity check of their own codes using Bait files.
iii. Infecting such programs will, therefore, increase the chances of the virus getting detected.
Killing activity of anti-virus software
There are some viruses that avoid detection by anti-virus software by killing the task associated with anti-virus software.
Making stealth virus
i. There is some strong virus that tricks anti-virus software by intercepting its requests.
ii. The virus can then return an uninfected version of the file to anti-virus software so that it assumes that the file is “clean”.
Virus analysis
IDA pro tools
Programs For Ethical Hacking
– IDA pro ethical hacking tools is dissembler and debugger tool
– It can run on multiple operating systems such as Windows, Mac OS X, Linux, etc.
– It can be used in source code analysis, vulnerability research as well as reverse engineering
Autorun virus remover
- Autorun is the built-in feature of Windows OS that allows the application to run automatically from USB/CD drives as soon as they are connected to the system.
- This feature is often exploited by viruses to spread from one system to another.
- Autorun virus remover helps in removing the virus that comes along with external storage such as USB/CD drives.
Related Articles
Ethical Hacking Programs For Free
This has been a Beginner’s guide to Ethical Hacking Software. Here we discussing in terms of ethical hacking software means gaining unauthorized access to data in a system or computer.